What CISOs Need to Know About OpenClaw
Share This Story, Choose Your Platform!
Security leaders do not adopt tools because they sound innovative. They adopt them because they reduce risk in a measurable way, integrate into existing controls, and do not quietly expand the attack surface.
That is the lens CISOs should apply when evaluating OpenClaw.
OpenClaw is an open-source, agentic AI assistant that can take actions across systems and workflows, which is exactly why it has drawn both excitement and security scrutiny. (Reuters)
Whether OpenClaw is positioned as a security platform, an infrastructure component, or a new operational layer, the core question remains the same.
Does it strengthen resilience, or introduce new complexity disguised as progress?
This article outlines what CISOs should focus on before OpenClaw becomes embedded in the enterprise.
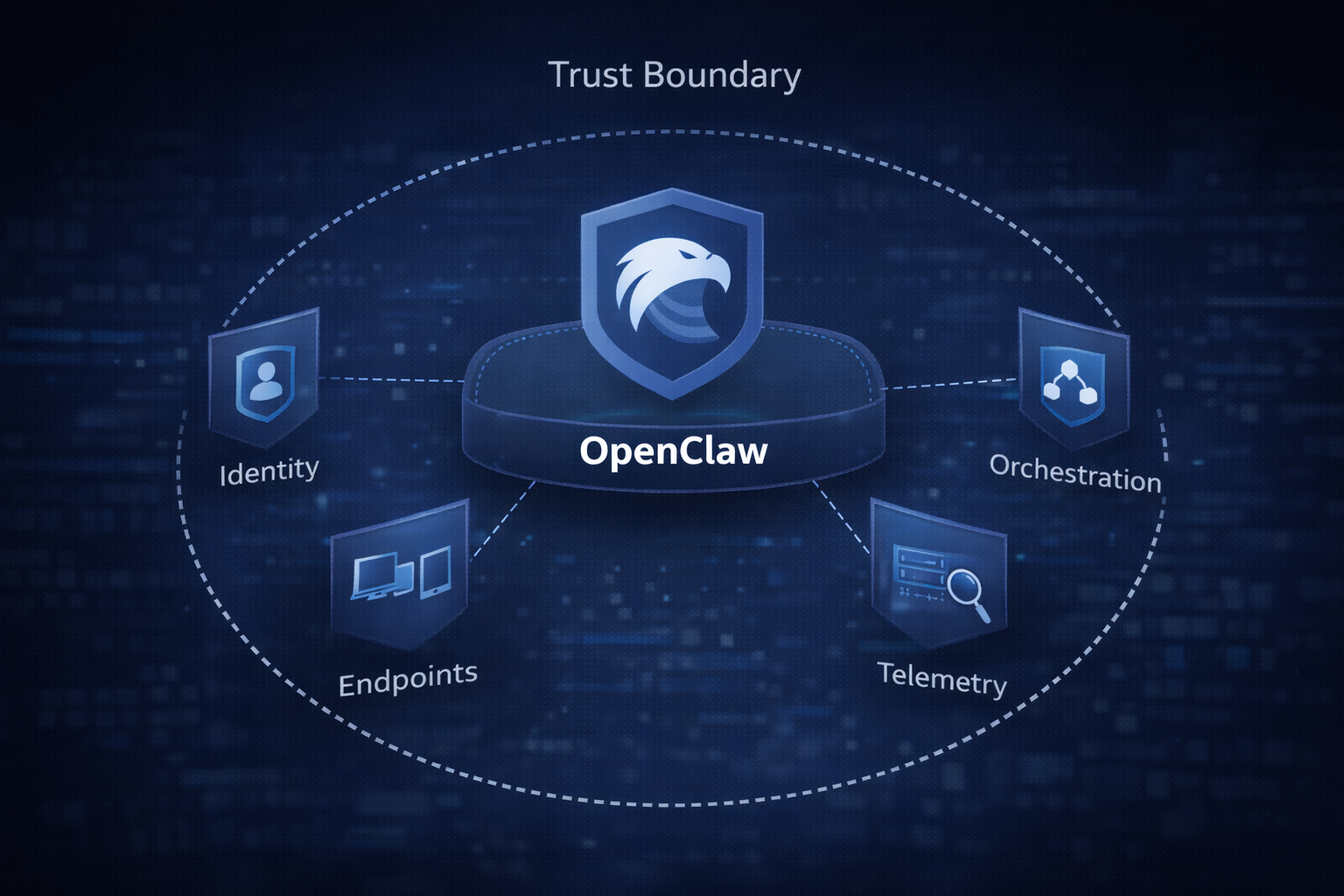
1. OpenClaw Is Not Just a Tool. It Is a Trust Boundary.
The first mistake organizations make with new platforms is treating them like another vendor SKU.
If OpenClaw touches identity flows, privileged access, endpoint execution, orchestration pipelines, or telemetry streams, it is no longer “just a tool.” It becomes a trust boundary.
(H4) CISOs should ask
What systems does OpenClaw sit between
What privileges does it require to function
What happens if it is compromised
Any platform with broad integration becomes a high-value target, and recent reporting has highlighted real-world concerns about misuse, exposed configurations, and unpredictable behavior in agentic tools. (WIRED)
2. Security Posture Depends on Architecture, Not Branding
CISOs should demand architectural clarity, not marketing reassurance.
Key questions
Is OpenClaw centralized or distributed
Does it introduce a new control plane
What are the failure modes
Does it degrade gracefully, or catastrophically
A modern platform should reduce fragility, not concentrate it. If OpenClaw becomes a choke point for automation, identity, or execution, it becomes a choke point for compromise.
3. Data Handling and Telemetry: What Does OpenClaw See
Agentic platforms run on visibility. That means OpenClaw may ingest logs, behavioral telemetry, endpoint metadata, user activity, and sensitive operational signals.
CISOs should clarify
Where this data is stored
Who can access it
Whether it is encrypted at rest and in transit
Retention policy and deletion controls
Whether it crosses regulatory boundaries
If OpenClaw becomes a telemetry hub, it becomes a compliance object, and security teams should treat it with the same rigor they apply to SIEM, SOAR, and identity logs. (SOPHOS)
4. Identity and Privilege: The Real Attack Surface
Every meaningful security platform eventually becomes an IAM problem.
If OpenClaw requires elevated access to perform tasks, CISOs need to enforce strict controls that prevent privilege sprawl.
Required safeguards
Role-based access control aligned to job function
Least privilege enforcement by default
Privileged session monitoring for elevated actions
Strong separation of duties for configuration and approval
Regular access reviews and drift detection
The uncomfortable truth is that many enterprise incidents are privilege failures, not malware failures. If OpenClaw expands privilege sprawl, it increases risk.
5. Integration Risk: Does OpenClaw Simplify or Multiply Complexity
CISOs are already managing stack entropy. OpenClaw should not add another isolated layer.
It must integrate cleanly with core systems such as SIEM and SOAR, EDR and XDR, IAM and PAM, cloud security posture management, and incident response workflows.
If adoption means “yet another console,” operational cost can exceed the benefit.
Security teams evaluating OpenClaw should explicitly map: tool-to-tool integrations, event flow, ownership of alerts, and remediation handoffs before rollout. (CrowdStrike)
6. Governance: Who Owns OpenClaw Internally
A neglected question is the most dangerous question.
Who is accountable after OpenClaw is deployed?
Security platforms fail when ownership is ambiguous.
CISOs should define
Operational owner (SecOps, IT Ops, cloud team)
Patch and update responsibility
Escalation paths and incident playbooks
Audit cadence and reporting expectations
Configuration baselines and change control
Technology without governance is latent exposure.
7. Vendor Risk and Supply Chain Reality
If OpenClaw is externally developed or community maintained, CISOs should evaluate supply chain integrity with the same rigor they apply to enterprise software.
Minimum due diligence
SBOM availability and update cadence
Vulnerability disclosure practices
Incident transparency history
Third-party dependency risk
Update signing and integrity verification
A platform cannot be secure if its supply chain is opaque, and recent public discussion has emphasized risks in the broader OpenClaw ecosystem, including malicious add-ons and exposed instances. (The Verge)
8. The Strategic Question: What Problem Does OpenClaw Actually Solve
The final filter is brutal, but necessary.
CISOs should require clear answers
What risk is reduced
What cost is removed
What capability is gained
What happens if we do nothing
If OpenClaw does not map to a defined security outcome, it is noise.
CISOs do not buy novelty. They buy risk reduction.
Conclusion: OpenClaw Should Earn Its Place in the Security Architecture
OpenClaw may represent a meaningful shift, but CISOs should approach it with disciplined skepticism, especially given recent coverage of organizational bans and security concerns tied to agentic behavior and ecosystem risks. (WIRED)
The evaluation framework is simple:
Trust boundaries
Privilege implications
Telemetry governance
Integration realism
Operational ownership
Supply chain exposure
Measurable security outcomes
If OpenClaw strengthens resilience without inflating complexity, it deserves attention.
If it expands the attack surface under the guise of innovation, CISOs should walk away.
Get Started Now
If your team is evaluating agentic AI platforms or automation layers, the safest next step is a structured security and governance assessment before production adoption.
Complete the form below to request an Agentic AI Security & Governance Assessment.